
Hi all, last Wednesday Microsoft released Windows 11 Insider Preview Build 25992 to the Canary Channel.
Close to smooth upgrades here, One device did not continue past 37% installing in the 1st phase, a simple pause updates & resume fixed it.
SMB is getting more secure, might break some stuff but fixing a more secure communication is best.
Happy Upgrades!
What’s new in Build 25992
SMB Changes
Starting with this build (Build 25992), we are introducing the following Server Message Block (SMB) protocol changes.
SMB firewall rule changes: Creating SMB shares changes a longtime Windows Defender Firewall default behavior. Previously, creating a share automatically configured the firewall to enable the rules in the “File and Printer Sharing” group for the given firewall profiles. Now, Windows automatically configures the new “File and Printer Sharing (Restrictive)” group, which no longer contains inbound NetBIOS ports 137-139. We plan future updates for this rule to also remove inbound ICMP, LLMNR, and Spooler Service ports and restrict down to the SMB sharing-necessary ports only.
This change enforces a higher degree of default of network security as well as bringing SMB firewall rules closer to the Windows Server “File Server” role behavior. Administrators can still configure the “File and Printer Sharing” group if necessary as well as modify this new firewall group.
For more information on this change, review https://aka.ms/SMBfirewall. For more information on SMB network security, review Secure SMB Traffic in Windows Server.
SMB NTLM blocking exception list: The new SMB NTLM blocking feature first announced in Windows 11 Insider Preview Build 25951 now supports specifying exception lists for NTLM usage. This allows an administrator to configure a general block on NTLM usage while still allowing clients to use NTLM for specific servers that do not support Kerberos, either because they are not Active Directory domain joined or are a third party without Kerberos support.
For more information on this change, review https://aka.ms/SmbNtlmBlock.
SMB alternative client and server ports: The SMB client now supports connecting to an SMB server over TCP, QUIC, or RDMA using alternative network ports to the hardcoded defaults. Previously, SMB only supported TCP/445, QUIC/443, and RDMA iWARP/5445. In addition, the SMB over QUIC server in Windows Server also supports endpoints configured with different ports than 443 (this option will be part of a separate Windows Server Insider Preview release). Windows Server does not support configuring alternative SMB server TCP ports, but third parties such as Samba do.
You can specify an alternative SMB client port using the NET USE command and New-SmbMapping PowerShell cmdlet. You can also completely disable this feature with a group policy.
For more information on using this option, review https://aka.ms/SMBAlternativePorts. For more information on configuring non-standard SMB server ports in third parties, consult their product documentation.
SMB over QUIC client access control certificate changes: The SMB over QUIC client access control feature first announced in Windows 11 Insider Preview Build 25977 now supports using certificates with subject alternative names and not just a single subject. This means the client access control feature now supports using a Microsoft AD Certificate Authority and multiple endpoint names, just like the currently released version of SMB over QUIC. You can now evaluate the feature using the recommended options and not require self-signed test certificates.
For more information on this change, review https://aka.ms/SmbOverQUICCAC. For more information on SMB over QUIC, review https://aka.ms/SMBoverQUIC.
Changes and Improvements
[File Explorer]
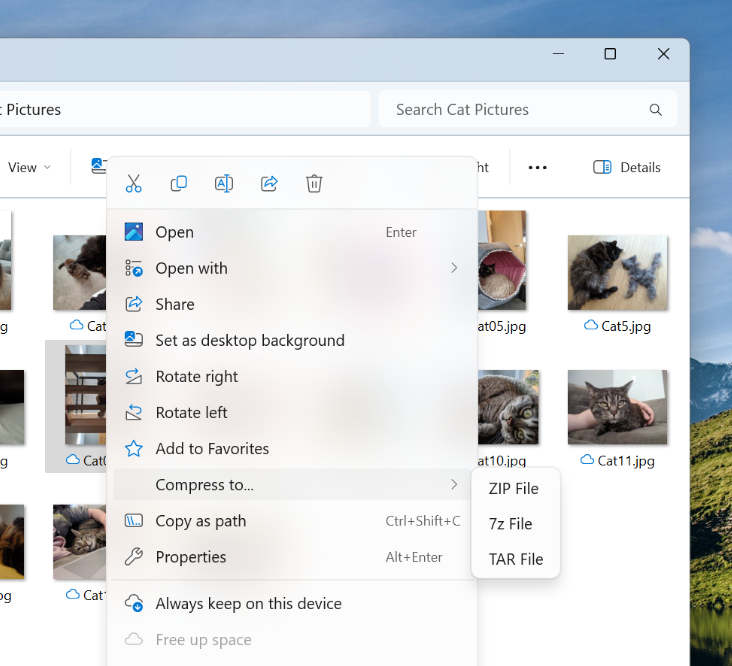
- Did some work which should help noticeably improve the performance of opening large .zip files in File Explorer.
- [ADDED] We’ve added support for creating 7-zip and TAR archives in addition to ZIP.
[Snap Layouts]
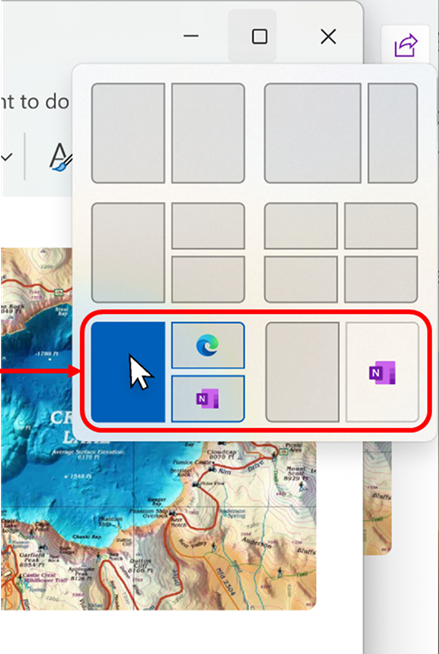
- [ADDED] We will show suggestions in Snap Layouts that help you instantly snap multiple app windows together. When hovering over the Minimize or Maximize button on an app (or WIN + Z) to launch the layout box, you will see app icons displayed in various layout options to help recommend the best layout option that works best.
Fixes for known issues
- We fixed the issue causing blank options to show on the Personalization and Privacy & Security settings pages, where if clicked on it would crash Settings.
- Fixed an issue causing the context menu to draw off screen when invoked using touch or pen on the side of your desktop.
- Fixed an issue where Settings Home might show a prompt to sign into your Microsoft account, and fail to sign in if you tried to use it, even though Settings itself showed you were already signed in.
- If you were experiencing Quick Settings crashes and WIN + A not working in the previous flight, that should be resolved now.
- Fixed an issue that was causing taskbar icons to disappear after switching desktops.
Known issues
- [REMINDER] Some popular games may not work correctly on the most recent Insider Preview builds in the Canary Channel. Please be sure to submit feedback in Feedback Hub on any issues you see with playing games on these builds.
- We’re working on a fix for an issue where attempting to reboot into safe mode hangs on the boot logo.
- [NEW] Attempting to navigate to Settings > Bluetooth & Devices > Touchpad on this build will crash Settings.
Snipping Tool Update
We are rolling out Snipping Tool (version 11.2310.49.0) to Windows Insiders in the Canary and Dev Channels improving HDR display support. Screenshots and screen recording on displays with HDR enabled should be able to better display colors.
source: Windows Blogs


 Get Your Microsoft Trainings here:
Get Your Microsoft Trainings here:
