Most IT-Pro’s I talk to on this topic have the same answer when it comes to catching a possible virus on a machine.
Important steps to take:
- Remove the device from the corp network
- Scan the device with the ‘favorite’ antivirus product
- If the step above fails to find it, use another antivirus/antimalware product
- …..
- clean install the device
There are a few problems with this approach
- Scanning an entire machine depending on the hardware and amount of files on the system can take hours per product
- only at the end of the scan you know if you picked the right product to catch the malware
- you only get 1 opinion at a time
As most know, there’s no perfect antivirus product, though many do a good job.
What if we could get the knowledge of all those vendors combined in one scan action?
The knowledge is out there!
https://www.virustotal.com is a website that allows you to upload a suspicious file & check it against most of the known vendor’s engines.
Upload is only needed if the file isn’t already known in their database, if anyone already uploaded the file you want to test a simple file-hash check reveals the latest scan result of the file
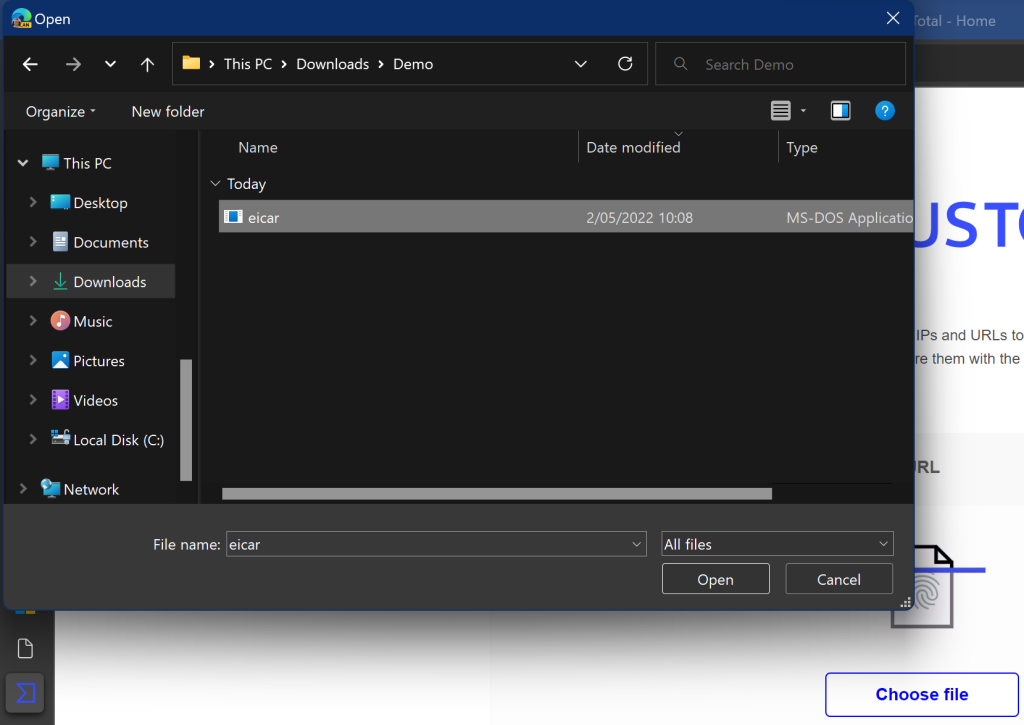
press choose file on the file tab & select a file to upload/check
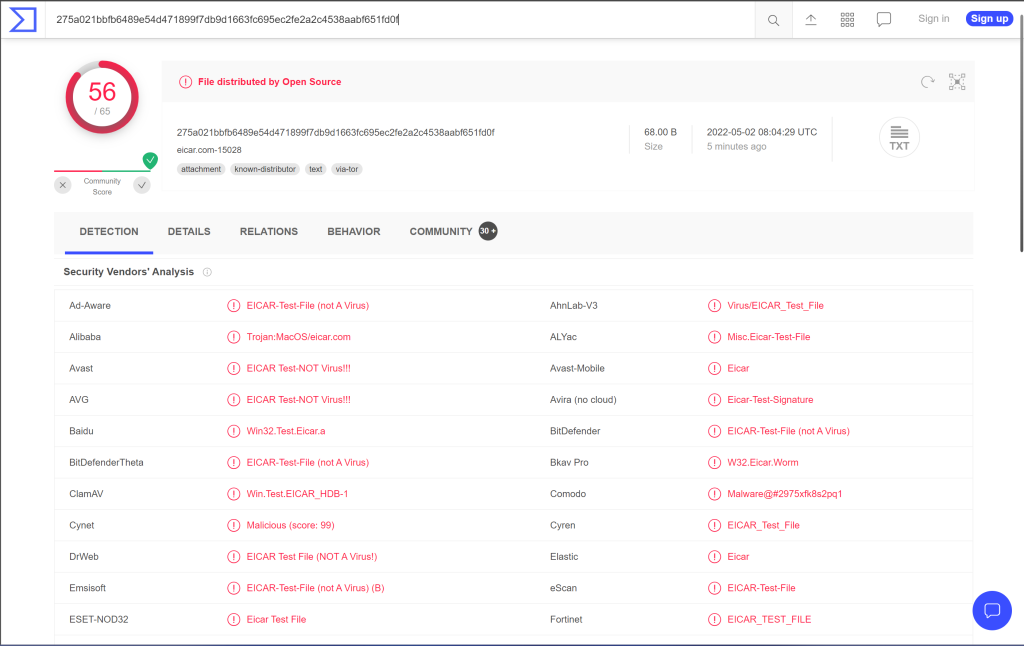
For this demo I used the eicar.org test file a well known test virus
As this is a know file no scan was needed & the result is instant, you can access the result >here<
If you want to update the result, rescan the file with all those engines (this one was scanned 5 minutes ago at the time of the test) you can press the circle arrow at the top right.
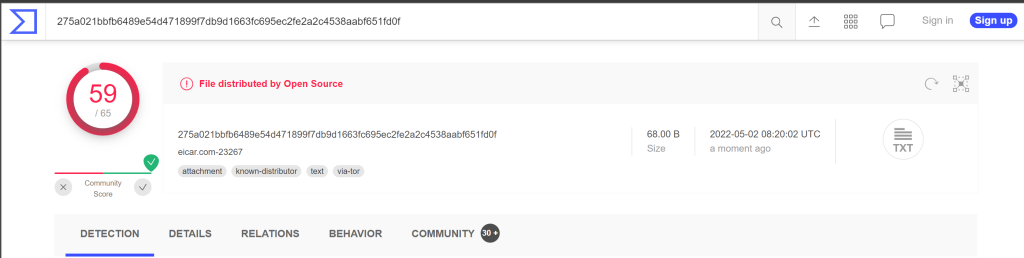
The number of used engines can vary from time to time & type of file, some engines do not can certain filetypes
looking at the list in this result you will be able to spot you favorite tools & more.
So now we are able to scan a file with all the possible intel, solving the issue of what engine to use to catch the malware
A good Idea to use this when assessing the use of a new tool
More on how to extend this to more than just 1 file in ‘part 2’